Here is a detailed review of bluetooth technology which covers all important aspects of bluetooth starting from its working to its applications in our daily life.
Origins of Bluetooth
- Bluetooth began as an open standard project in 1994 by Ericsson in Sweden
- It was originally named multi-communicator (MC) link—not a very memorable name
- The goal was to develop a wireless communication standard that would support short-range voice and data transfers amongst multiple devices.
- Four years later, in 1998, four other companies, IBM, Intel, Nokia, and Toshiba, joined with Ericsson to form a special interest group (SIG)
- SIG was to promote the standard and promptly renamed the standard to Bluetooth (a much more memorable name).
- Today, the promoter group consists of nine companies
- 3Com, Lucent Technologies,Microsoft, Motorola, IBM, Intel, Nokia, Toshiba, and, of course, Ericsson
- There are also hundreds of associate and adopter member companies
- The Bluetooth SIG is driving a low-cost short-range wireless specification for connecting mobile devices
- Bluetooth was coined from the name of a tenth-century Danish king, Harold Bluetooth
- The Viking king was credited with uniting Norway and Denmark during his reign.
- The promise of Bluetooth is seamless interconnectivity among devices
- Uniting technologies like the king
- Computers, wireless headsets, printers, personal digital assistants (PDAs), mobile phones, and laptops will be able to share files and transfer both voice and data
Introduction to Bluetooth
- Bluetooth is a global wireless standard that in its simplest form is designed to replace cables.
- The cost must be extremely low, and the devices must be easy to operate.
- Additionally, the devices must be robust
- Because Bluetooth devices operate in the unlicensed ISM band at 2.4 GHz.
- The ISM band is reserved for the general use of devices that operate to specifications determined by the various geographical governing bodies such as the Federal Communications Commission (FCC) in the United States and European Telecommunications Standards Institute (ETSI) in Europe.
- The ISM band is unlicensed
- This means that anyone can operate a wireless device in the band
- As long as it adheres to the regulations specified in the particular geographical location
- Other bands require a license (which is expensive) and adherence to government regulations for said spectrum.
- In contrast to the ISM band, one of the 3G UMTS bands in Europe covers a spectrum from 1,900 to 1,980 MHz.
- Providers wishing to offer 3G services must obtain an expensive license to do so.

- In the ISM band you can find a myriad of short-range devices for many applications
- Like wireless local area network (WLAN) applications
- And of course, all of our microwave ovens (operating at 2.45 GHz)
- Bluetooth devices must combat the noisy and overcrowded environment of the ISM band
- And it does so by employing three critical techniques to minimize interference from other devices
- Frequency-hopping spread spectrum (FHSS), short data packets, and adaptive power control
Frequency Hopping
- lSince the ISM band is already crowded, it is highly likely that multiple devices attempting to transmit at the same frequency will coexist.
- lTo limit interference in the unlicensed ISM band, the FCC regulations place limits on maximum power transmission
- lThe regulation permits a transmit power level only up to 0 dBm
- lThis is really not enough power to ensure reliable operation of the wireless network
- lTo circumvent this challenge and still comply with the regulations, a frequency-hopping spread spectrum (FHSS) technique with a hop speed of 1,600 hops/s is used.
- lUsing FHSS, the power level can be as high as 20 dBm
- lAnd the range of the wireless network can be extended to 100m
- lFrequency hopping acts to spread the power across the ISM band
- lAnd, thus, still adheres to the 0-dBm regulation, provides robust communications, and also acts as a means of security
Bluetooth Modulation
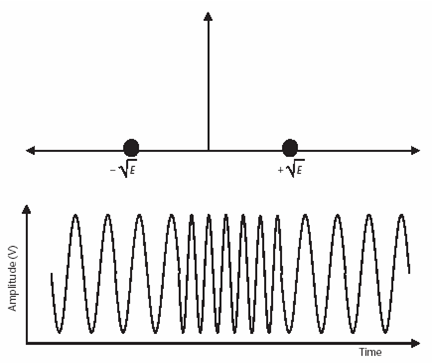
- Bluetooth uses Gaussian frequency shift keying (GFSK)
- More explicitly, Bluetooth uses 0.5 BT Gaussian-filtered two-frequency shift keying (2FSK)
- Also referred to as binary frequency shift keying (BFSK) at 1 Msymbol/s with a channel spacing of 1 MHz
- Since only two frequencies are used, one bit is one symbol
- How?
- That is a 1 indicates a positive frequency deviation (nominally +157.5 kHz) from the carrier
- And a 0 indicates a negative frequency deviation (nominally –157.5 kHz) from the carrier
- Figure on next slide shows the amplitude versus time, as well as a constellation diagram plot of 2FSK modulation that is used for Bluetooth
- The frequency deviation range is between 140 and 175 kHz.
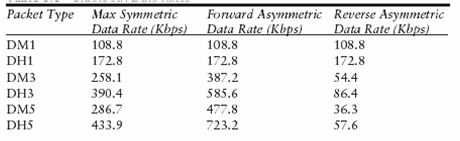
 Bluetooth Data Rates and Data Packets
Bluetooth Data Rates and Data Packets
- The theoretical maximum data rate is 1 Mbps
- But due to overhead, the maximum realizable asymmetric data rate is reduced to 723.2 Kbps
- This is also a bit misleading because the reverse link has a much lower data rate
- Table on next slide is a summary of the possible data rates for the various packet sizes
- The information is transmitted in a packet in a time slot
- Each time slot corresponds to an RF hop frequency
- A packet of information can be transmitted in one time slot, three time slots, or five time slots.
- Naturally, a five-slot packet carries more information than a three-slot packet, which carries more than a one-slot packet
- Data high (DH) rate achieves higher data rates by using less error correction in the packets
- Data medium (DM) rate achieves a lower bit error rate probability by using more error correction in the packets
- A Bluetooth packet is shown in next slide
- The packet contains a 72-bit access code, a 54-bit header, and a 0 to 2,745-bit payload
- The access code is subdivided into a 4-bit preamble, a 64-bit synchronization word, and a 4-bit trailer
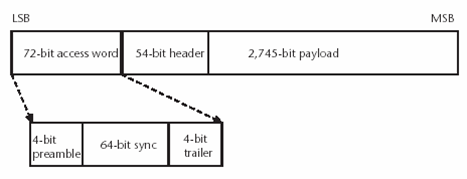
- This information is important to understand because the various wireless tests that are performed often use or do not use portions of the packet,
- And the test system must be able to isolate to a specific region in the packet
- For example, the initial carrier frequency tolerance (ICFT) is determined by measuring the frequency deviation of the 4-bit preamble of a DH1 packet
- So the test system must be able to distinguish among the various subsections of the packet
- Another example is the carrier frequency drift, where the drift frequency is determined by measuring the frequency of the payload and using the preamble as the initial reference frequency
Adaptive Power Control
- Recall that regulations limit the transmit power to 0 dBm
- If higher transmit power levels are desired, then a spread spectrum technique must be utilized
- There are three power classes defined in the Bluetooth specification
- Table on next slide lists the classes along with their corresponding maximum transmit output powers and power-level control range
- Power class 3 is the most common class being adopted by manufacturers
- Why?
- Simple fact that class 3 consumes the least amount of power.
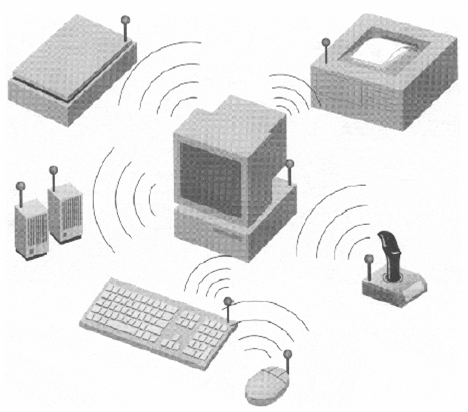
Bluetooth Usage Models : The Cordless Computer
Bluetooth Usage Models : The Ultimate Headset
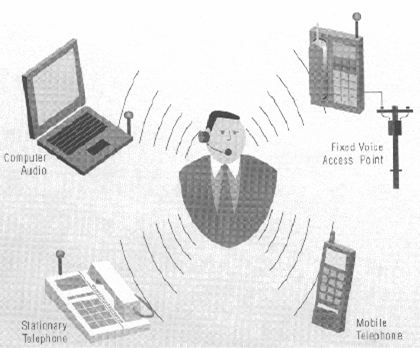
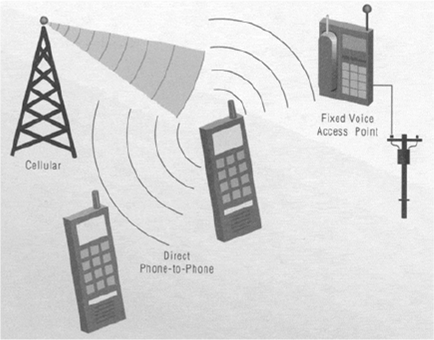
Bluetooth Usage Models:The Three-in-One Phone
Bluetooth Usage Models: The Three-in-One Phone
- A key benefit of the three-in-one phone is that a single telephone could become the only one that a person needs
- If multiple voice access points using Bluetooth wireless communication become available in environments such as the home, office and public areas, a single personal telephone that is usable almost anywhere becomes realistic
- The need for separate telephones and separate telephone numbers in the office, at home and while traveling could be reduced
- Another benefit that derives from the use of such voice access points is the possibility for reduced cellular airtime charges
- When the handset is used as a cordless phone, communicating with a standard “landline” telephone service via an access point, no cellular airtime charges need be incurred.
- The direct telephone-to-telephone, or “walkie-talkie” function of the three-in-one phone usage model is most useful with the 20 dBm power amplified radio, with its range of 100 meters
- 10 meters is enough..?
- However, even with the standard radio with its 10-meter range there are situations where the direct phone-to-phone communication might be useful
- These might include cases such as:
- people communicating across different floors of a building
- from within confined spaces or
- when non-intrusive communication is desired even when both parties might be able to see each other ( for example, video and sound control workers in a crowded auditorium)
Bluetooth Usage Models:The Interactive Conference (File Transfer)
The Bluetooth internet bridge usage case 2: direct local area network access through a data access point
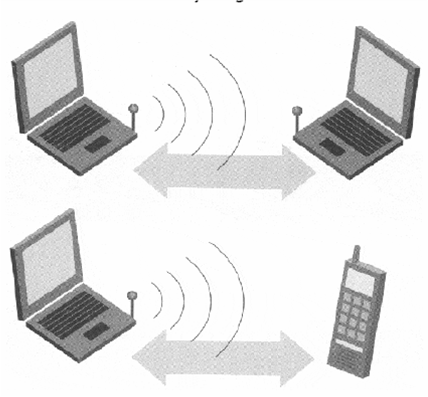
Bluetooth Usage Models: The Speaking Laptop
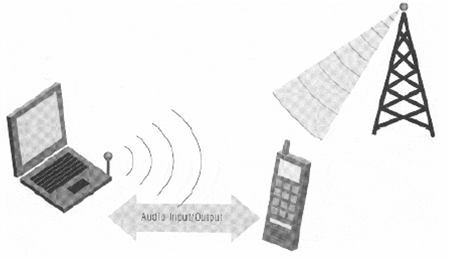
Bluetooth Usage Models: The Speaking Laptop
- The speaking laptop is one of the usage models that is not advertised in version 1.0 of the specification
- The concept behind it is that a laptop (or notebook) computer’s microphone and speaker could be used as the audio input and output for a voice call placed on a mobile telephone
- As an example, suppose someone places a call on a mobile phone during a meeting
- As the conversation progresses, it becomes evident that others in the meeting would benefit from taking part in the call
- Bluetooth wireless communication could be used to route the voice traffic to a notebook computer in the conference room, allowing the computer to be used as a speakerphone
- The call is still being carried over the mobile phone’s wide area voice network but the audio source and sink are now at the notebook computer.
Bluetooth Usage Models: The Automatic Synchronizer
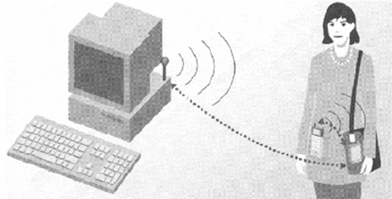
- Personal portable devices empower people to have quick and easy access to information they can use in their daily lives
- For that information to be most useful it needs to be kept up to date
- But this personal information management data might be distributed across the many devices that a person could use
- For example, new calendar entries or to-do list items might be entered on any of a notebook computer, personal digital assistant or smart phone
- Or these entries might be entered on a desktop computer and stored on a server in a network
- Synchronization is the process of merging the data from two different sources based upon some set of rules such that the resulting data sets are identical
- A common example is synchronizing a personal digital assistant with a desktop or notebook computer.
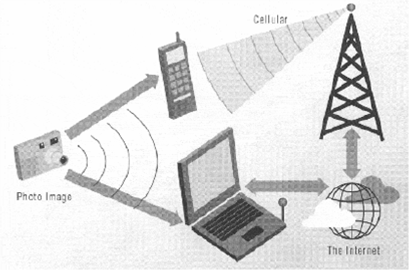
- The underlying concept is that of having a digital camera which can wirelessly transfer a photo image to some other device
- Which could then e-mail the image to a recipient, thus creatinga digital “postcard.“
- Today many digital cameras use a serial cable to transfer photo images to a computer
- Where they can be stored, catalogued, manipulated and distributed.
- Bluetooth wireless communication removes the need for a cable which in turn presents new ways to use a device
- This scenario is useful not only for sending “postcard” type pictures to friends and relatives but also for commercial applications, such as real estate (transferring photos of newly listed homes to a central database), law enforcement (transferring photos of suspects or stolen vehicles, for example) and insurance
Bluetooth Usage Models: Ad Hoc Networking
- Ad hoc networks are networks that form spontaneously
- Bluetooth wireless communication is an enabling technology for these sorts of applications
- The interactive conference usage model showed how objects such as electronic business cards or files could be exchanged in a conference room setting
- When ad-hoc networks can be formed among the meeting participants, additional applications become possible
- Among these are collaborative applications
- Such as real-time viewing and group editing of presentations and instant messaging among the meeting participants.
Bluetooth Usage Models: Hidden Computing
- Hidden computing involves a class of applications in which devices that are not overtly being used by a person can still perform tasks on that person’s behalf.
- We have already seen one example that could be considered a hidden computing application: the automatic synchronizer
- In that usage model, a PDA “hidden” in a pocket or purse could synchronize with another device without user intervention
- Several other examples have been described in the context of Bluetooth wireless communication such as:
- A notebook computer “hidden” in a briefcase in a “sleeping” mode could be configured to awake periodically, receive new e-mail and send information such as new e-mail alerts (and possibly a short clip of the e-mail content) to a mobile phone. The user might then decide to browse e-mail using the mobile phone or process e-mail on the notebook computer.
- A mobile telephone “hidden” in a pocket or purse could be used by an appropriately configured notebook computer “hidden” in a briefcase to access a network in the manner described for the Internet bridge (dial-up networking) scenario. Once the computer is connected to a network in this fashion, network synchronization or transmission and reception of e-mail could be initiated, all without conscious user interaction with either device.
The Bluetooth Protocol Stack

A high-level view of the Bluetooth stack.
The Bluetooth Protocol Stack: Transport protocol group
- This group is composed of the protocols designed to allow Bluetooth devices to locate each other
- And to create, configure and manage both physical and logical links
- That allow higher layer protocols and applications to pass data through these transport protocols
- The protocols in this group include the radio, base band, link manager, logical link and adaptation and the host controller interface (HCI)
The Bluetooth Protocol Stack: Middleware protocol group
- The middleware protocol group includes both third-party and industry standard protocols and protocols developed by the SIG specifically for Bluetooth wireless communication
- The former includes Internet-related protocols (PPP, IP, TCP, and so on), wireless application protocols (WAP), object exchange protocols adopted from IrDA and the like
- The latter includes three protocols with a designed awareness of Bluetooth communications that facilitate a large number of other applications to run over Bluetooth links
- A serial port emulator protocol called RFCOMM enables legacy applications that normally would interface with a serial port to operate seamlessly over Bluetooth transport protocols
- A packet-based telephony control signaling protocol provides for advanced control of telephony operations
- Such as group management and mobility support for cordless handsets and base stations
- Finally, a service discovery protocol permits devices to discover each other’s services and to obtain information on how to access those services
The Bluetooth Protocol Stack:Application group
- This group consists of the actual applications that make use of Bluetooth links
- These applications could be legacy applications that are unaware of Bluetooth transports
- Such as a modem dialer application or a web-browsing client
- Or they might be aware of Bluetooth wireless communication
- For instance, applications that use the telephony control protocol for controlling telephony equipment
StumbleUpon | Digg | Reddit | Tweet | Facebook | Technorati | Delicious | Ping.fm | Slashdot






{ 0 comments… add one now }